The protection of private information and sensitive data has never been more important than it is today when digitization has come to be seen as a sign of advancement. Australia, like many other nations, has realized the value of privacy and cybersecurity regulations to protect its people and businesses from the constantly expanding threat of cybercrime. In this thorough guide, we’ll examine Australia’s cybersecurity and privacy legislation with a focus on the fight against cybernetic crime, a threat that still looms big over the internet. Australia has strengthened its cybersecurity and privacy framework by taking important steps. The country is aware that risks exist in the digital sphere and that neglecting to protect critical information might have dire repercussions. By creating standards, guidelines, and penalties for non-compliance, cybersecurity and privacy regulations are created to solve these difficulties.
The Rise of Cybernetic Crime
Understanding the formidable foe that Australian cybersecurity and privacy laws strive to confront, cybernetic crime is essential before digging into the specifics of those laws. Data breaches, hacking, identity theft, and other illegal activities are all included in this harmful and dynamic category of criminal behavior. Cybercriminals pose a serious threat to both persons and organizations by taking advantage of weaknesses in digital systems and networks.
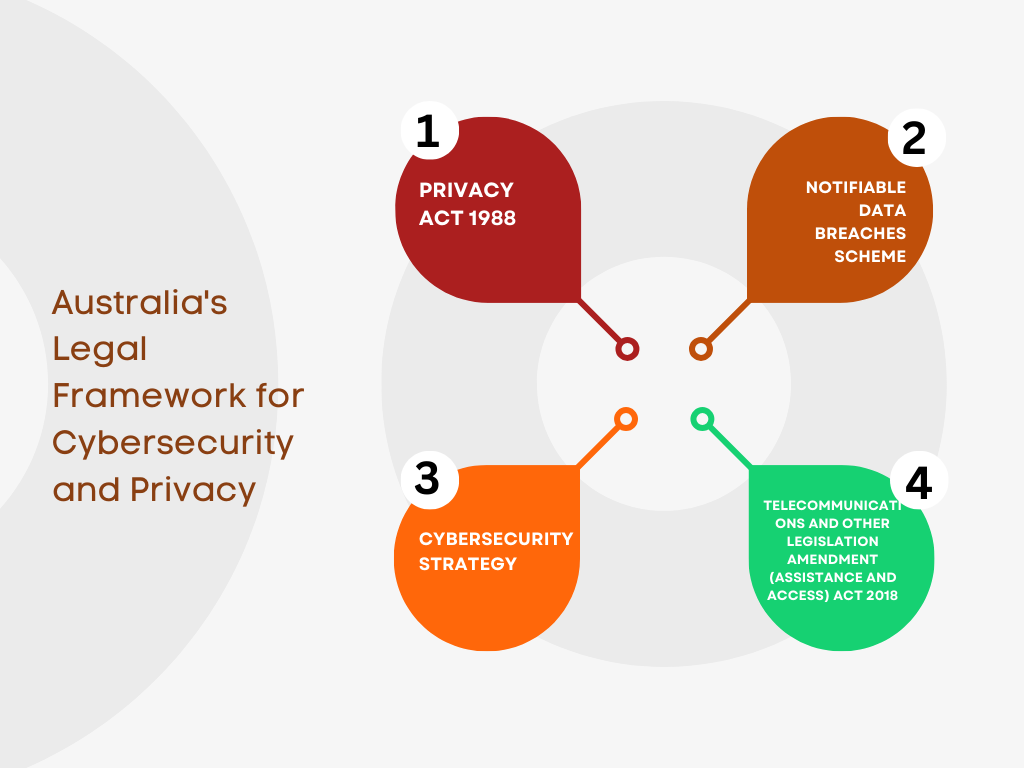
Cybersecurity Laws in Australia
Australia has strengthened its cybersecurity position by enacting a number of laws and regulations. A key law governing how businesses handle personal information is the Privacy Act of 1988, which underwent significant revisions in 2017. It lays up requirements for companies, authorities, and nonprofits with regard to the gathering, using, and disclosing of personal data.
Additionally, organizations are required to notify persons affected by data breaches under the Notifiable Data Breaches (NDB) scheme, which was implemented in 2018.
The Security Legislation Amendment (vital Infrastructure) Act 2021, which acknowledges the significance of protecting vital infrastructure from cyber threats, is one of the most recent advancements.
Privacy Laws in Australia
The Privacy Act of 1988, which, as was previously indicated, underwent significant revisions in 2017, serves as the primary framework for privacy regulations in Australia. The Australian Privacy Principles (APPs), a set of rules for handling personal information, are outlined in the Act. Aiming to achieve a compromise between personal privacy and legitimate commercial interests, it also provides guidelines for the acquisition, storage, and dissemination of personal data.
In charge of monitoring privacy compliance and resolving concerns about privacy, the Office of the Australian Information Commissioner (OAIC) is crucial.
Combating Cybernetic Crime: A Collaborative Effort
Cybernetic crime is a battle that cannot be won by any one entity on its own. To protect the digital sphere, the Australian government, businesses, and people all have important roles to play. Effective cyber threat identification and mitigation depend on collaboration.
The Australian Cyber Security Centre (ACSC), which offers resources, direction, and incident response coordination, acts as a focal point for cybersecurity information.
Staying Compliant with Australian Cybersecurity and Privacy Laws
Australia’s cybersecurity and privacy rules must be followed, but doing so is also essential to a company’s risk management strategy. Violations of the law can have serious repercussions, such as expensive fines and harm to one’s reputation.
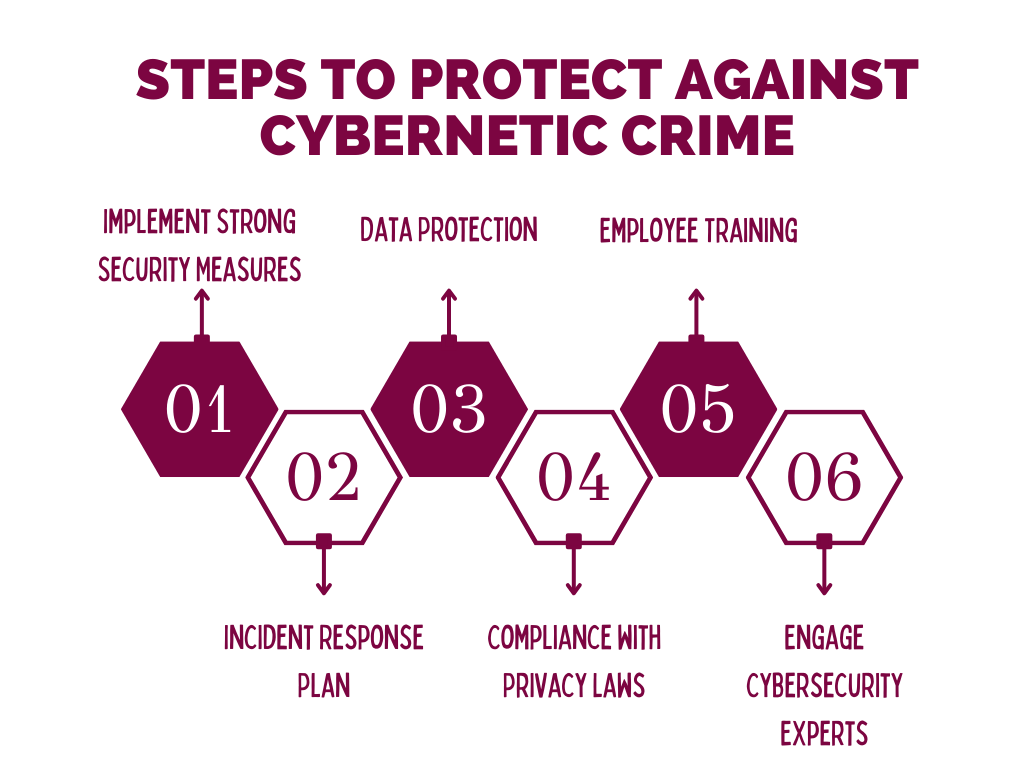
To ensure compliance, organizations should consider the following steps:
- Data Protection Measures: Implement strong data protection measures, such as access limits, encryption, and frequent security audits.
- Employee Training: Employee education on cybersecurity best practices and awareness-building about the dangers of cybercrime.
- Incident Response Plans: To quickly lessen the effect of data breaches or cyberattacks, develop and test incident response protocols.
- Privacy Impact Assessments: To detect and manage privacy issues in data processing operations, and conduct privacy impact analyses.
- Engage Legal Counsel: To successfully navigate the complicated regulatory environment, seek legal assistance with experience in cybersecurity and privacy legislation.
The Future of Cybersecurity and Privacy in Australia
The sophistication of cyber threats will increase as technology does. The Australian government is well aware of this and is dedicated to advancing privacy and cybersecurity regulations in order to stay on top of the game. The best course of action for both individuals and corporations is to remain informed and proactive.
Protecting Australia Through Business Law and Ethics Assignment
In conclusion, Australia’s cybersecurity and privacy laws provide an essential line of defense against the growing threat of cybercrime. For organizations working in the digital age, understanding and abiding by these regulations is not only a legal duty but also an ethical necessity. Businesses must make sure they are not only abiding by the letter of the law but also upholding the highest ethical standards in their practices as they negotiate the complexity of cybersecurity and privacy.
Do not hesitate to contact Assignment Unlocked if you are studying business law and ethics and need aid with your assignments. Our professionals are here to assist you in completing your business law and ethics assignment successfully and ensuring that you have a firm understanding of the moral and legal standards that guide Australia’s cybersecurity and privacy regulations.
Are you prepared to ace your law and ethics assignment? Call Assignment Unlocked right away for knowledgeable advice and assistance. Learn the fundamentals of business law and ethics assignment with the help of our devoted team of experts. Your achievement is only a click away!






